
1)
To determine: Whether anyone can read the message.
Introduction:
1)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
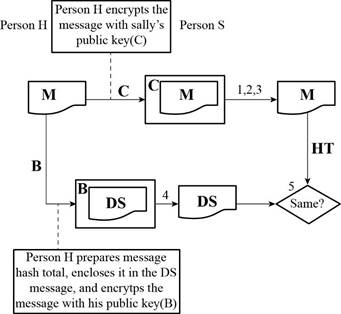
Given diagram:
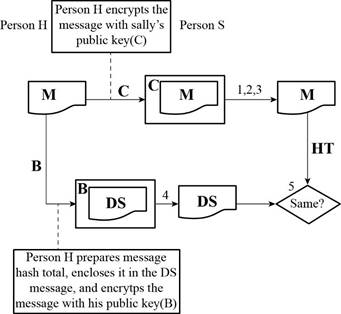
Here,
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether anyone can read the message:
Not everyone can read the message. Only the person who has the private key of Person S can be able to open the message.
2)
To determine: Whether Person S can be sure that the message is from Person H.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
2)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
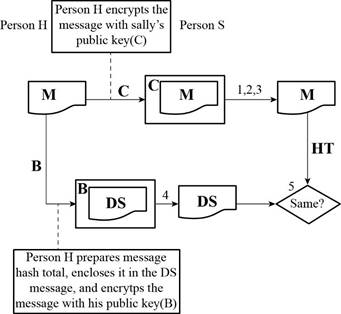
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether Person S can be sure that the message is from Person H:
Anyone with the public key of Person S can be able to send the message
3)
To determine: Whether digital signature message is secret.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
3)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
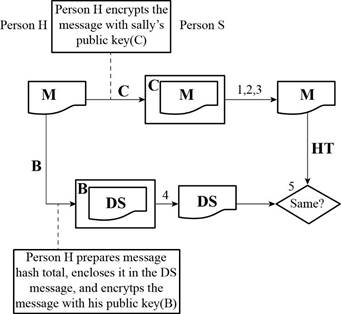
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether a digital signature message is secret:
Anyone with the public key of Person H can be able to open the digital signature message.
4)
To determine: Whether someone other than Person H can send the digital signature message.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
4)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
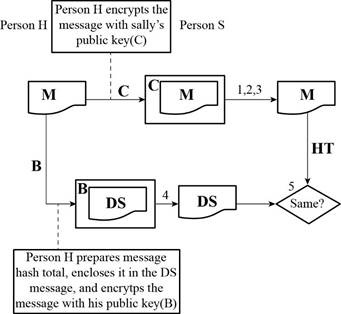
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether someone other than Person H can send the digital signature message:
A person with the private key of Person H can be able to send the digital signature message.
5)
To determine: How Person S know that the message has not been corrupted in transit.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
5)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine how Person S know that the message has not been corrupted in transit:
If the hash total of digital signature equals the hash total that Person S calculated from the message then the message has not been corrupted in transit.
6)
To determine: The sub-part that is related to authenticity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
6)
Explanation of Solution
Determine the subpart that is related to authenticity:
Subpart (2) and Subpart (4) are about authenticity.
7)
To determine: The sub-part that is related to integrity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
7)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to integrity:
Subpart (5) is about integrity.
8)
To determine: The sub-part that is related to confidentiality.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
8)
Explanation of Solution
Given diagram:
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to confidentiality:
Subpart (1) and Subpart (3) are about the confidentially.
Want to see more full solutions like this?
Chapter 9 Solutions
Accounting Information Systems
- Which of the following is not a way to prevent your computer from being attacked by ransomware? A. making sure your antivirus security programs are up to date B. opening all attachments from emails from unknown senders C. using secure (password protected) networks and backing up your files regularly D. not using open Wi-Fi (nonpassword, nonencrypted) in public locationsarrow_forwardWhich preventive, detective, and/or corrective controls would best mitigate the following threat, and why? (c) A criminal remotely accessed a sensitive database using the authentication credentials (user ID and strong password) of an IT manager. At the time the attack occurred, the IT manager was logged into the system at his workstation at company headquarters.arrow_forwardQuestion 11 To communicate electronically under a false identity for the purpose of obtaining someone's personal information. Your answer: O fraud O spoofing O spyware O vishing Clear answerarrow_forward
- Communication via the internet is fraught with major security problems. When it comes to Internet communications, which of these aspects poses the biggest security risk?arrow_forwardWhat are the risk management happened in the Scandal of Fraud about Wiredcard AGarrow_forwardOther than becoming a CFE, what could you do to become a fraud specialist? Please provide references with URL.arrow_forward
- Which of the following statements is correct? a. TCP/IP is the basic protocol that permits communication between Internet sites. b. TCP/IP controls Web browsers that access the Web. c. TCP/IP is the document format used to produce Web pages. d. TCP/IP is used to transfer text files, programs, spreadsheets, and databases across the Internet. e. TCP/IP is a low-level encryption scheme used to secure transmissions in higher-level (HTTP) format.arrow_forward“Organizations are encouraged to take every precaution possible to protect their information systems so that potential for fraud and any resulting losses can be significantly minimized.” Required: Critically explain any three motives behind the cheque fraud scheme. What to do if someone has deposited a fake cheque into your bank account?arrow_forwardA digital signaturea. is the encrypted mathematical value of the message sender’s name.b. is derived from the digest of a document that has been encrypted with the sender’s private key.c. is derived from the digest of a document that has been encrypted with the sender’s public key.d. is the computed digest of the sender’s digital certificate.e. allows digital messages to be sent over an analog telephone line.arrow_forward
- Principles of Accounting Volume 1AccountingISBN:9781947172685Author:OpenStaxPublisher:OpenStax College
 Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,
Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,

